Zero Trust Architecture (ZTA) also known as Zero Trust Network Architecture is a modern Cybersecurity framework designed to enhance organisational security by eliminating the concept of implicit trust within networks. Unlike traditional security models that focus on securing the perimeter and assume anything inside is trustworthy, ZTA operates on the principle of “never trust, always verify.” Every user, device, and access request is treated as a potential threat until verified.
This approach aligns perfectly with today’s evolving Cybersecurity landscape, where businesses must contend with the challenges of remote work, cloud-based applications, and a growing number of IoT devices. By adopting ZTA, organisations can reduce their attack surfaces, prevent lateral movement of threats within their networks, and ensure data remains secure, no matter where it resides or how it is accessed.
Why is Zero Trust Architecture Essential?
Traditional security models, often referred to as the “castle-and-moat” approach, were built around securing a well-defined perimeter. These models worked effectively when applications and data resided within on-premises data centers, and users accessed resources from fixed locations. However, the digital transformation has drastically altered this paradigm.
With cloud computing, hybrid workforces, and increasing reliance on SaaS platforms, the perimeter has dissolved. Threats no longer come exclusively from outside the network; insider threats, compromised credentials, and advanced phishing attacks have made implicit trust a liability. Zero Trust Architecture addresses these challenges by requiring verification for every access request, regardless of origin.
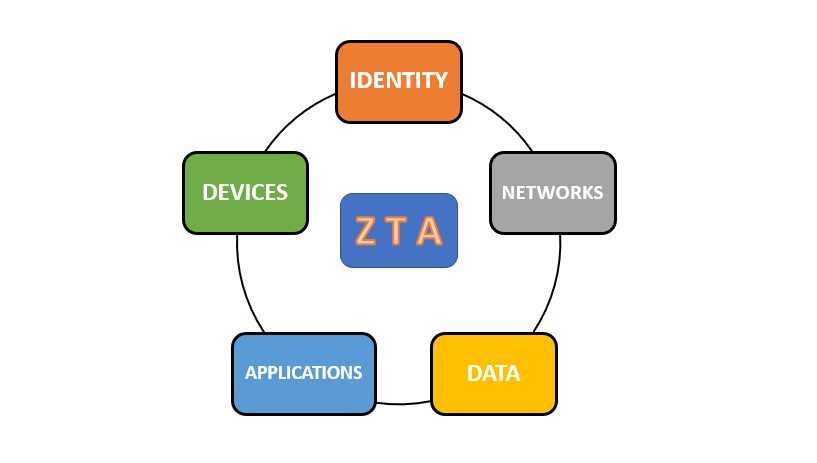
The Five Core Pillars of Zero Trust Architecture
Zero Trust Architecture is a comprehensive framework that encompasses five critical pillars: identity, devices, networks, applications, and data. These pillars ensure every aspect of an organisation’s digital ecosystem is secured.
- Identity: Ensuring that every user, whether an employee, contractor, or partner, is authenticated and authorised using multi-factor authentication (MFA) and strict access controls.
- Devices: Monitoring the security posture of all devices accessing the network, including endpoints like laptops, smartphones, and IoT devices, to ensure compliance with security standards.
- Networks: Segmenting networks to prevent lateral movement and using encrypted communication to secure data in transit.
- Applications and Workloads: Implementing identity-based access to applications and ensuring security measures are integrated into application workflows.
- Data: Adopting a data-centric security model that identifies, classifies, and protects sensitive information across its lifecycle, whether at rest, in transit, or in use.
By addressing these pillars, ZTA provides a multi-layered approach to security that adapts to the needs of modern organisations.
Benefits of Zero Trust Architecture
- Enhanced Security:
Zero Trust eliminates implicit trust, ensuring every user, device, and connection is verified before access is granted. This minimises the risk of unauthorized access and protects against evolving threats like ransomware and phishing attacks. - Reduced Attack Surface:
By implementing micro-segmentation and granular access controls, ZTA prevents attackers from moving laterally within the network. This significantly limits the damage that can be caused by a successful breach. - Stronger Data Protection:
ZTA adopts a data-centric approach to security. Sensitive information is identified, classified, and protected with encryption, access controls, and real-time monitoring, ensuring compliance with data protection regulations like GDPR and HIPAA. - Improved Incident Response:
With continuous monitoring and detailed logging, organisations can detect and respond to security incidents more quickly. Real-time insights enable faster containment of threats, reducing potential damage and downtime. - Adaptability to Modern Work Environments:
ZTA is built for the era of cloud computing, remote work, and BYOD (Bring Your Own Device). It enables secure access to resources from any location, on any device, without compromising security. - Enhanced User Experience:
While Zero Trust emphasises security, it also prioritizes efficiency. By leveraging adaptive policies and secure direct connections, users experience seamless access to resources without unnecessary delays. - Compliance and Governance:
ZTA simplifies adherence to regulatory requirements by providing robust security controls, detailed audit trails, and real-time compliance monitoring.
How Zero Trust Architecture Works
Zero Trust Architecture operates on the principle of continuous verification. It assumes that every entity—whether a user, device, or application—is potentially compromised and requires validation.
The process typically follows these steps:
- Verification of Identity and Context: Before granting access, ZTA verifies the user’s identity, device posture, and context, such as location and time of access. Multi-factor authentication and real-time behavioral analysis are commonly used for this purpose.
- Risk Assessment: Each access request is evaluated for potential risks. ZTA inspects traffic for threats and evaluates factors like device health and user behavior to assign a risk score.
- Policy Enforcement: Based on the risk assessment, adaptive policies determine whether access is granted or denied. If granted, the connection is made directly to the resource, bypassing traditional network pathways to reduce exposure.
- Continuous Monitoring: Even after access is granted, ZTA continuously monitors user activity and device behavior to detect anomalies and revoke access if necessary.
Steps to Implement Zero Trust Architecture
- Conduct a Security Assessment:
Begin by evaluating your organisation’s current security measures and identifying gaps that need to be addressed. This includes analysing user access patterns, device security, and existing network architecture. - Strengthen Identity and Access Management (IAM):
Implement multi-factor authentication (MFA) and identity-based access controls. Adopt least-privileged access principles to ensure users have only the permissions necessary for their roles. - Secure Devices and Endpoints:
Deploy endpoint protection tools and enforce strict security policies for all devices accessing your network. Regularly update and patch devices to address vulnerabilities. - Implement Network Segmentation:
Divide your network into smaller, isolated segments. This prevents lateral movement by attackers and ensures that a breach in one segment does not compromise the entire network. - Adopt Secure Access Tools:
Deploy tools like Zero Trust Network Access (ZTNA) to replace traditional VPNs. These tools provide direct, secure connections to applications without exposing the network. - Monitor and Analyse Traffic:
Use advanced analytics and continuous monitoring to detect and respond to potential threats. Invest in tools that provide real-time visibility into user activity and network traffic. - Educate Employees:
Train employees on the principles of Zero Trust and the importance of adhering to security policies. Awareness is a critical line of defense against threats like phishing and social engineering. - Partner with Experts:
Implementing Zero Trust Architecture can be complex. Partner with cybersecurity experts to ensure your strategy aligns with industry best practices and meets your organisation’s specific needs.
Zero Trust Architecture represents a fundamental shift in how organizations approach cybersecurity. By assuming nothing can be trusted and verifying every access request, ZTA provides a robust defense against modern threats. Its ability to adapt to cloud-based environments, remote work, and evolving attack surfaces makes it an essential framework for businesses of all sizes.
Contact Creative Networks Today
Need Help Implementing Zero Trust?
At Creative Networks, we specialise in designing and implementing tailored managed CyberSecurity that protect your business and empower your workforce.
Contact us today to learn how we can help you build a resilient, future-ready security architecture.




