Passwords remain the most common cause of breaches. In fact, Microsoft has confirmed that over 80% of Cyberattacks begin with stolen or weak passwords. Attackers exploit password reuse, brute force, and phishing at scale, and businesses pay the price.
Moving to Passwordless Authentication in Microsoft 365 with passkeys eliminates this risk while improving user experience. Passkeys are also a key enabler of phishing-resistant MFA, which is now considered best practice for enterprise security.
Recent studies show that users who switch to passkeys experience a 98% success rate in sign-ins, compared to just 32% with traditional passwords. Surveys also reveal that 53–61% of users find passkeys both easier to use and more secure than passwords.
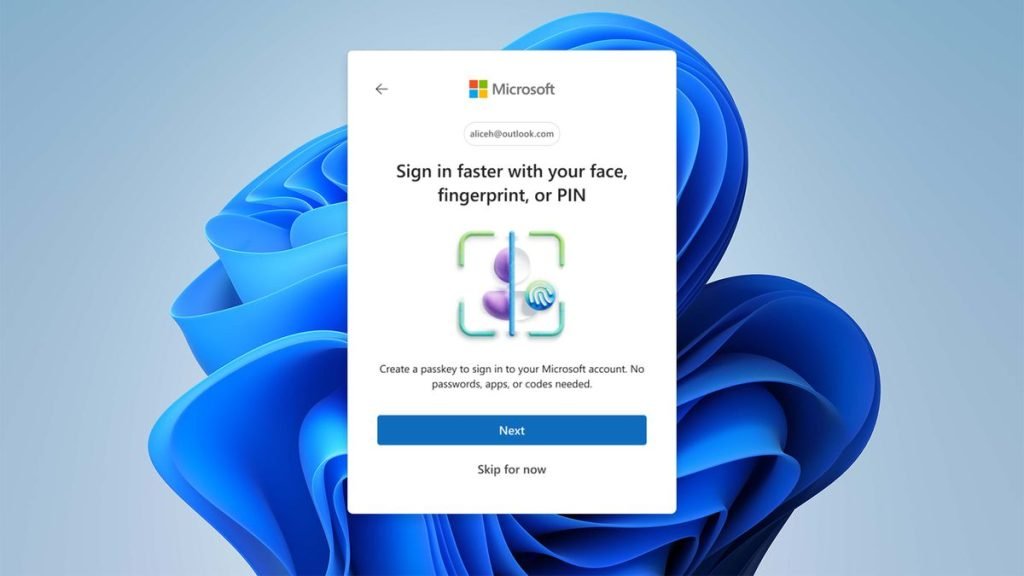
What are Passkeys in Microsoft 365?
Passkeys are a passwordless authentication method built on public/private key cryptography. A private key is stored securely on a device—such as a smartphone or hardware key—and is unlocked with a biometric or local PIN. The public key is registered with Microsoft 365.
Because there’s no shared secret to steal, passkeys are resistant to phishing and credential theft. For enterprises, the security benefits of passkeys in Microsoft 365 include fewer breaches, reduced reliance on weak MFA methods, and a smoother experience for end users.
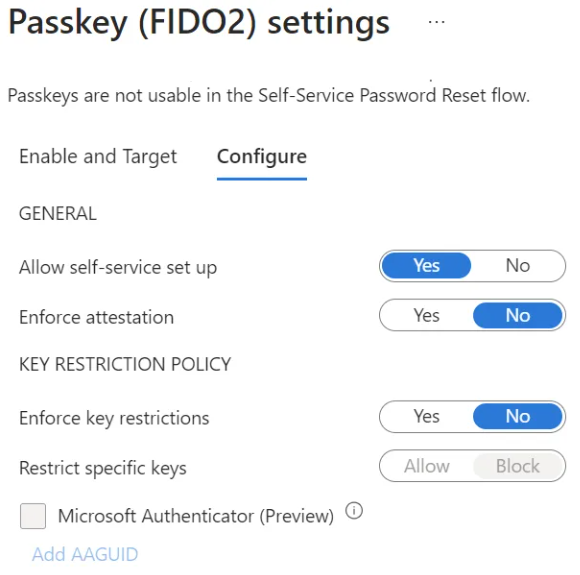
How to enable passkeys in Microsoft Entra ID
Passkeys can be rolled out in Microsoft 365 through Microsoft Entra ID (formerly Azure Active Directory). Admins can enable:
- Passkeys in Microsoft Authenticator, allowing users to sign in with device-bound credentials.
- FIDO2 security keys, ideal for shared devices, frontline staff, or administrators.
- Conditional Access authentication strengths, which let you enforce phishing-resistant MFA policies for specific apps, roles, or user groups.
With these tools, organisations can create a clear Microsoft 365 passkey policy with Conditional Access that gradually reduces reliance on passwords.
A Practical Microsoft 365 Passkey Rollout Plan
Rolling out passkeys across a Microsoft 365 tenant is best achieved in phases. Here’s a structured step-by-step passkey deployment plan that enterprises can follow.
Phase 0 – Prepare & Assess
Licensing and roles
Ensure you have the needed licensing for Conditional Access (for many tenants this is Microsoft 365 Business Premium or Entra ID P1). Assign the right admin roles (Authentication Policy Admin, Conditional Access Admin).Combined registration
Enable combined registration so users manage MFA and SSPR in one place. Require at least two methods per user.Break-glass accounts
Create two emergency cloud-only accounts exempt from Conditional Access. Store credentials offline with strong controls. Do not enable passkeys on these accounts.
Phase 1 – Pilot Deployment
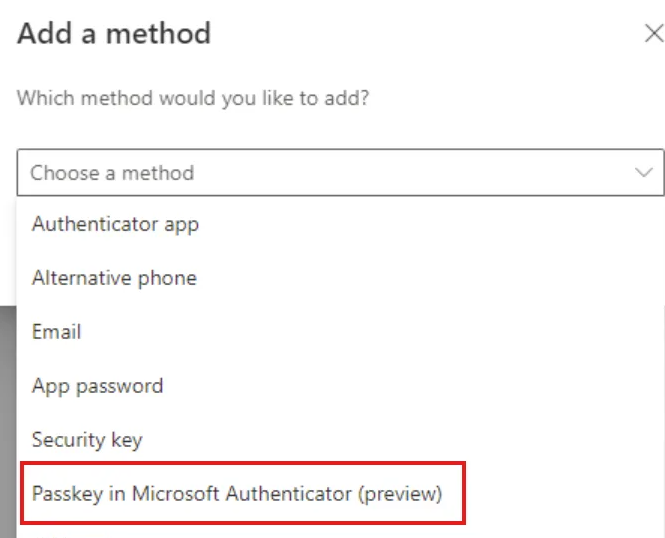
Enable methods
In Entra admin, enable FIDO2 and passkeys in Microsoft Authenticator for a pilot security group.Register users
Ask pilot users to register a passkey in Authenticator; admins and frontline users can also register a FIDO2 key.Try a soft policy
Create a Conditional Access policy for a non-critical app that requires the Passwordless authentication strength. Set it to Report-only, monitor sign-ins, then move to On.
Phase 2 – Expand and Harden
Enforce more apps and groups
Gradually expand the policy to more applications and user groups. Target departments that are most ready first.Protect high-risk roles
Require the Phishing-resistant authentication strength for administrators and sensitive roles (finance, HR, executives). Pair with Privileged Identity Management where applicable.Windows sign-in where needed
For shared devices or higher assurance, enable FIDO2 for Windows sign-in. Keep a small pool of spare keys per site.
Phase 3 – Optimise the Experience
- Migrate or isolate legacy protocols (such as IMAP/POP or older line-of-business apps).
- Ensure every user has at least two phishing-resistant methods registered.
- Provide helpdesk playbooks for lost devices or key replacement.
- Monitor metrics: the percentage of users registered with passkeys, adoption rates of passwordless logins, and helpdesk ticket trends.
Phase 4 – De-emphasise Passwords
- Tighten Conditional Access so that sensitive apps require only phishing-resistant MFA.
- Retire password-only sign-in paths.
- Communicate the benefits to end users: fewer resets, faster logins, and improved security.
Best Practices For Enterprises
- Start with pilots before enforcing policies tenant-wide.
- Use Conditional Access in report-only mode to gather insights before applying controls.
- Maintain highly restricted break-glass accounts for emergencies.
- Avoid weakening policies for legacy apps—re-platform or isolate instead.
- Track adoption rates and present them as part of wider Microsoft 365 security best practices.
- Document evidence to support compliance frameworks like Cyber Essentials, Cyber Essentials Plus, or ISO 27001.
What Success Looks Like
Organisations that implement a well-structured Microsoft 365 passkey rollout plan typically achieve:
- 70–80% of staff registered a passkey within three months
- 50–70% of interactive logins using passwordless authentication
- 100% of admins and privileged roles behind phishing-resistant MFA
- 40–60% fewer password reset tickets raised with the helpdesk
- Consistent evidence of compliance with industry standards
Frequently Asked Questions
Do we still need hardware keys if we use Authenticator?
Not always. Many businesses go Authenticator-first and issue FIDO2 security keys only to admins or frontline workers.
Will passkeys work across Microsoft 365 apps and browsers?
Yes. Passkeys work on modern web, mobile, and desktop apps across Microsoft 365 when properly configured in Entra ID.
What Microsoft 365 license do I need?
Conditional Access authentication strengths require at least Entra ID P1, which is included in Microsoft 365 Business Premium.
Final Thoughts
Passwords are no longer enough. By following a Microsoft 365 passkey rollout plan, you can migrate from traditional credentials to passwordless authentication, enforce phishing-resistant MFA policies, and reduce your risk significantly. Passkeys make authentication both safer and more user-friendly—a rare combination.
Contact Creative Networks Today
At Creative Networks, we deliver secure passwordless transformations for enterprises:
- Strategy & readiness: licensing checks, role assignment, pilot planning
- Deployment: enabling passkeys in Microsoft Entra ID, distributing FIDO2 keys, configuring Conditional Access policies
- Optimisation: staff training, legacy app migration, adoption monitoring, and compliance evidence
Contact Creative Networks today to start your Microsoft 365 passkey rollout and make phishing-resistant MFA the standard across your business.




