Cybersecurity threats are continually evolving, and one of the most persistent and damaging types of attacks is the Denial of Service (DoS) attack.
This blog post by Creative Networks will explore what is a Denial of service attack (DoS), how it works, its impact, and measures you can take to protect your organisation.

What is a Denial of Service (DoS) Attack?
A Denial of Service (DoS) attack is a malicious attempt by cybercriminals to disrupt the normal functioning of a targeted server, service, or network by overwhelming it with a flood of internet traffic. The primary goal is to render the target inaccessible to its intended users, effectively causing a “denial of service.” This can lead to significant operational, financial, and reputational damage.
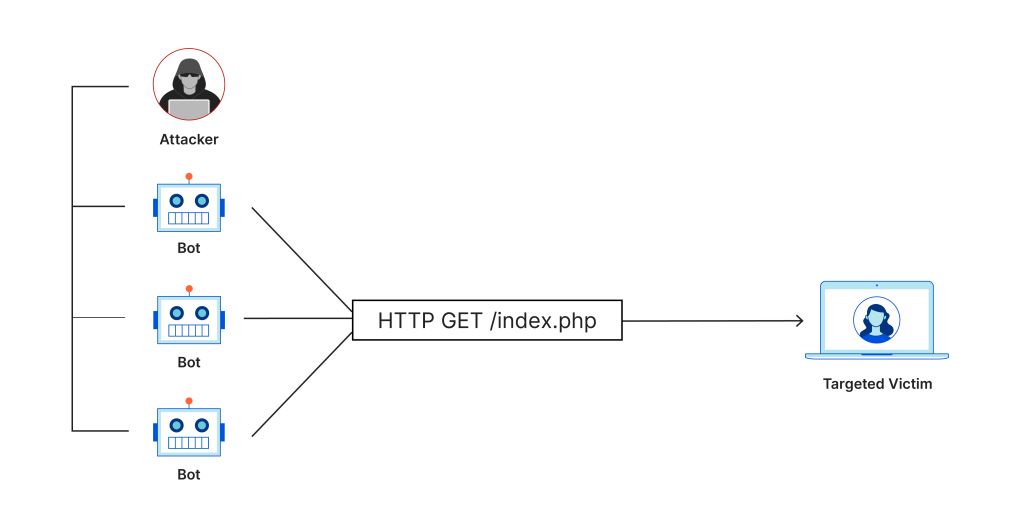
How DoS Attacks Work
In a DoS attack, attackers use a variety of methods to flood a target system with an excessive amount of traffic. This can exhaust the system’s resources, such as CPU, memory, and bandwidth, leading to a slowdown or complete shutdown of the service. Here are the basic mechanisms of a DoS attack:
Flooding Attacks:
The attacker sends a massive number of requests to the target server, overwhelming its capacity to handle the traffic. Common flooding attacks include:
- ICMP Flood (Ping Flood): Overloads the target with ICMP Echo Request (ping) packets.
- UDP Flood: Sends large numbers of UDP packets to random ports, causing the target to check for the application at each port.
- SYN Flood: Exploits the TCP handshake process by sending a succession of SYN requests without completing the handshake, consuming server resources.
Crash Attacks:
The attacker exploits vulnerabilities in the target system to cause it to crash. For example, by sending malformed packets that the system cannot handle.
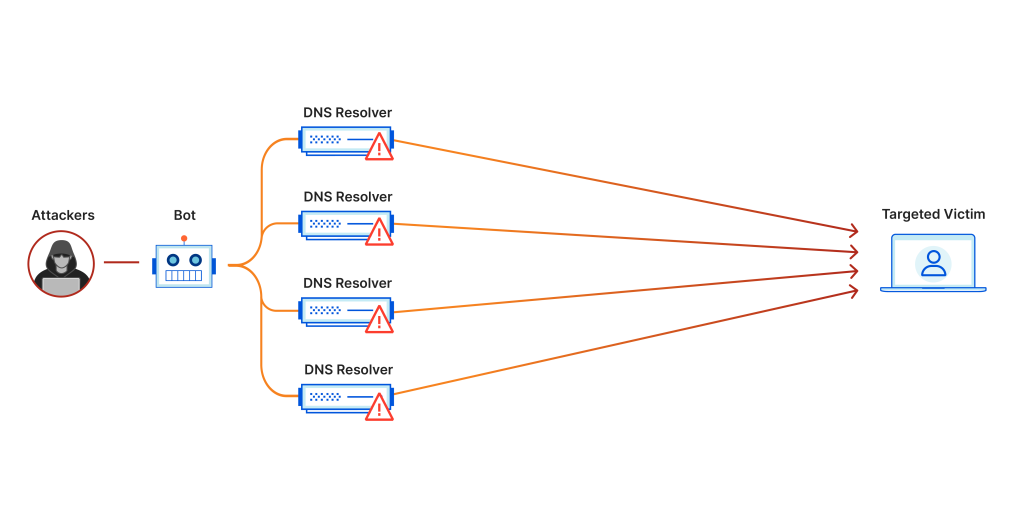
Distributed Denial of Service (DDoS) Attacks
A Distributed Denial of Service (DDoS) attack is a more advanced form of DoS attack where the attack is launched from multiple compromised devices, often part of a botnet. A botnet is a network of infected computers controlled remotely by the attacker. By leveraging the power of multiple devices, a DDoS attack can generate much more traffic than a single-source DoS attack, making it more difficult to defend against.
How Cybercriminals Create and Use Botnets
Cybercriminals create botnets by spreading malware that infects computers, turning them into “bots” that can be controlled remotely. This is often achieved through phishing emails, malicious downloads, or exploiting software vulnerabilities. Once a computer is infected, it becomes part of the botnet and can be used to launch a coordinated attack against a chosen target
Impact of DoS Attacks
DoS attacks can have devastating consequences for organizations, including:
- Financial Losses: Disrupted services can lead to significant revenue losses, especially for e-commerce sites and financial institutions. The inability to process transactions or provide services can result in direct financial damage.
- Reputational Damage: Inaccessible services can damage the reputation of an organization, leading to a loss of customer trust and loyalty. Customers expect reliability, and repeated outages can drive them to competitors.
- Operational Disruptions: Critical operations can be halted, affecting productivity and service delivery. For businesses that rely on online services, this can cripple day-to-day operations and result in long-term setbacks.
Why Do Cybercriminals Launch DoS Attacks?
There are several motivations behind DoS attacks:
- Activism: Some attackers, known as hacktivists, launch DoS attacks to protest against or disrupt organizations they disagree with. These attacks are often ideologically driven and aim to make a statement or disrupt services as a form of protest.
- Financial Gain: Attackers may demand a ransom to stop the attack, effectively extorting money from the victim. This is known as ransom-based DDoS (RDoS).
- Competitive Advantage: Rival companies might use DoS attacks to disrupt competitors’ services. Although illegal, such attacks can be used to gain a temporary market advantage.
- Political Motives: In some cases, state-sponsored actors use DoS attacks to disrupt governmental or critical infrastructure as part of cyber warfare.
How to Protect Against DoS Attacks

Early Detection
Spotting a DoS attack early can help mitigate its impact. Monitor your website’s traffic for unusual spikes that could indicate an ongoing attack. Large spikes in traffic might be a result of a DoS attack, especially if they don’t correlate with marketing activities or other expected traffic surges.
Technical Measures
Router and Network Configuration:
- Limit the router to prevent the web server from being overwhelmed.
- Add filters to drop packets from obvious sources of attack.
- Time out half-open connections more aggressively.
- Drop spoofed or malformed packets.
- Set lower SYN, ICMP, and UDP flood drop thresholds.
Web Hosting Services:
- Use a reliable web hosting service that can handle large amounts of traffic and has measures in place to defend against DoS attacks.
- Cloud-based hosting services often offer better protection and scalability compared to self-hosted servers.
Internet Service Provider (ISP) Support:
- Keep emergency contacts for your ISP readily available. They can provide support and may have the capacity to mitigate the attack.
Defensive Technologies
Firewalls and Intrusion Detection Systems (IDS):
- Firewalls can be configured to reject suspicious traffic.
- IDS can monitor and alert on unusual activity, enabling quicker response to potential threats.
Content Delivery Networks (CDNs):
- CDNs can absorb and distribute the excess traffic generated by DoS attacks, reducing the burden on the target server.
Load Balancers:
- Load balancers can distribute traffic across multiple servers, preventing any single server from being overwhelmed.
Organisational Measures
Incident Response Plan:
- Develop and maintain an incident response plan specifically for dealing with DoS attacks.
- Ensure that your IT team is trained and prepared to respond quickly.
Regular Security Audits:
- Conduct regular security audits to identify and address potential vulnerabilities that could be exploited in a DoS attack.
Understanding and preparing for DoS attacks is crucial for any organization that relies on its online presence. By implementing robust security measures and maintaining vigilance, you can minimize the risk and impact of these disruptive attacks.
Contact Creative Networks Today
Ready to Strengthen Your Cybersecurity?
At Creative Networks, we specialize in comprehensive cybersecurity solutions tailored to your needs. Our experts can help you develop a robust defense strategy to protect against DoS attacks and other cyber threats.
Contact us today to enhance your cybersecurity posture and safeguard your digital assets.
Get Started Now!




